Lifespan of TLS certificates is getting reduced to 47 days
Published on April 23, 2025 by Mattias Geniar
In a pretty significant shift for internet security and subsequently certificate management, the CA/Browser Forum has officially voted to reduce the maximum validity period of TLS certificates to just 47 days by March 15, 2029.
This move aims to enhance digital security and trust across the web. But as these changes approach, it'll become increasingly crucial for organizations to understand their implications and prepare accordingly. Automation will likely become mandatory.
What's the deal with TLS certificates? #
What are they?
TLS (Transport Layer Security) certificates—more commonly known as SSL certificates—are digital certificates that authenticate the identity of a website and enable encrypted connections like HTTPS.
Why do I need one?
Well, they are essential for securing data transmitted between a user's browser and a web server, ensuring privacy and data integrity. This is pretty important, as SSL certificates are now a requirement for all websites, as mandated by Google and Mozilla. In a nutshell, they enable:
- Data Encryption: Protecting sensitive information from eavesdroppers.
- Authentication: Verifying that a website is legitimate.
- Trust: Your browser will mark all HTTP pages as "Not Secure".
What are the upcoming changes to certificate lifetimes? #
To keep a short story even shorter, the maximum certificate lifetime is going down pretty drastically. The idea is, by reducing the lifetimes, you need more frequent validation ergo potentially compromised certificates won't stick around for too long. Here's the rundown.
- Until March 15, 2026, the maximum lifetime for a TLS certificate is 398 days.
- March 15, 2026, the maximum lifetime for a TLS certificate will be 200 days.
- March 15, 2027, the maximum lifetime for a TLS certificate will be 100 days.
- March 15, 2029, the maximum lifetime for a TLS certificate will be 47 days.
Some additional clarification, though. As of March 15, 2029, the maximum lifetime for a TLS certificate will indeed be 47 days, but the maximum period during which domain validation information may be reused is only 10 days. That's pretty short. Manual revalidation will still be possible, but this kind of sets you up for trouble if you're not diligent.
What does this mean for my business and website(s)? #
The proposed changes are put there to improve overall security on the web. However, that is assuming everyone handles their certificate renewals precisely on schedule. While shorter lifetimes do improve security, they also increase the risk of certificate expiration without you realized it. Failing to renew your TLS/SSL certificate means browsers will immediately block access to your site.
We probably don't have to paint this picture, but if your site becomes inaccessible because of an expired TLS certificate, this can lead to:
- Lost revenue
- Damaged brand trust
- Search engine ranking drops
- Internal panic and/or angry clients
As a side note, according to the 2023 EMA report, 25% of certificates pose a security threat because they're either expired or self-signed. As lifetimes shrink, that number will go up considerably if counter measures aren't taken.
How do I prepare for these changes? #
The good news is that it's actually pretty easy to avoid certificates from expiring. There's plenty of time left and solutions are already readily available:
- The most obvious solution would be to automate TLS certificate renewals. Using services like Let’s Encrypt, cloud providers with automated certificate management, or something like CertBot you can deal with these shorter lifespans without breaking much of a sweat.
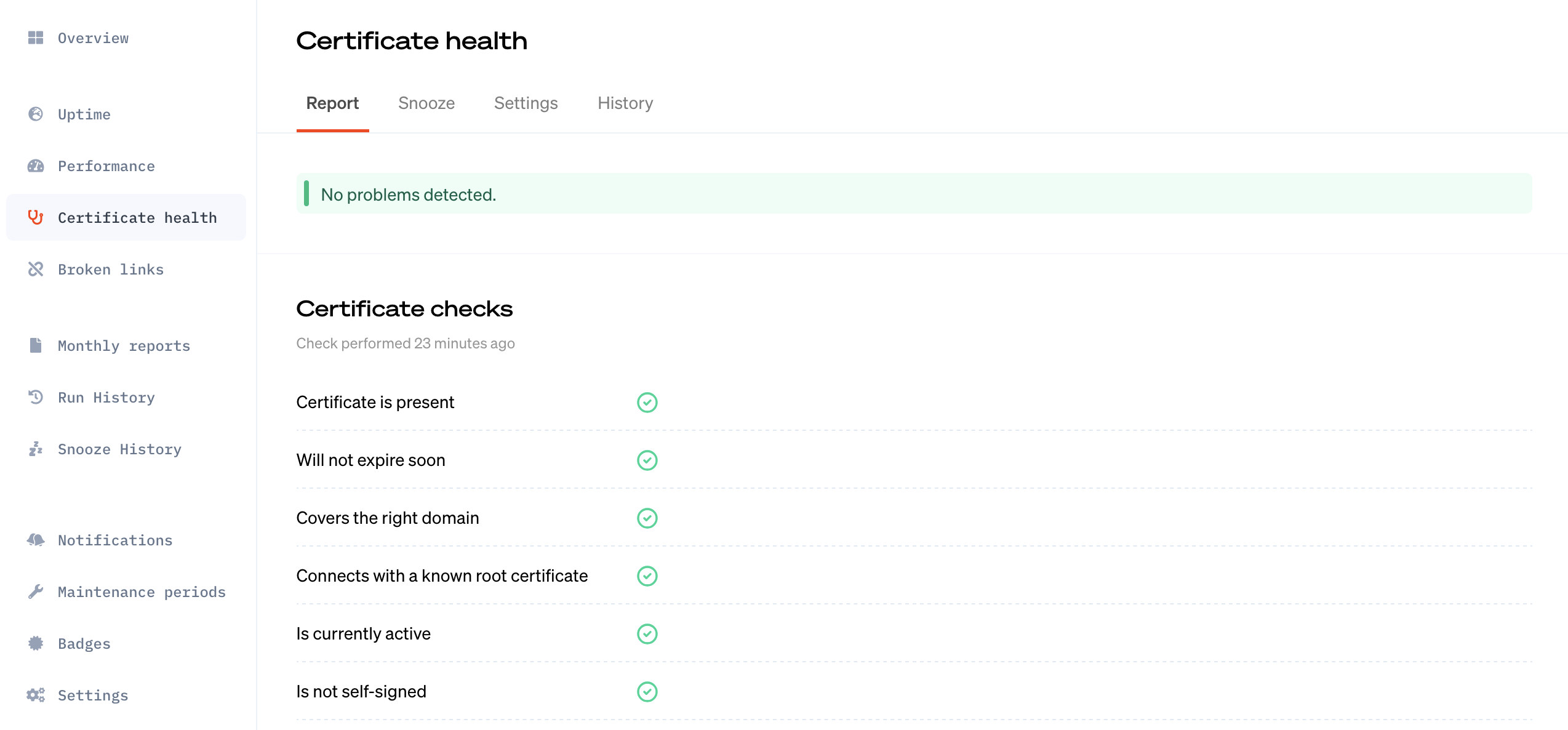
- Another solution is to simply monitor your websites, which is just good practice either way. A website monitoring tool (like Oh Dear, obviously) can notify you in time of not only expired certificates, but of broken links, tasks, drops in performance, SEO...
- Lastly, it's never a bad idea to keep your team informed. Make sure your developers, DevOps engineers, and sysadmins understand the timeline and implications of these changes.
Closing thoughts #
In a nutshell, the ballot argues that shorter lifetimes are necessary because the information contained in these certificates becomes less trustworthy over time, which can only be mitigated by revalidating said information more frequently.
DigiCert, the certificate authority where we got this information from, expects rapid adoption of automated certificate renewal well before the 2029 changes. This is the most likely course of events. But we wouldn't be Oh Dear if we didn't tell you to also use website monitoring :)