The nightmare scenarios we prevent
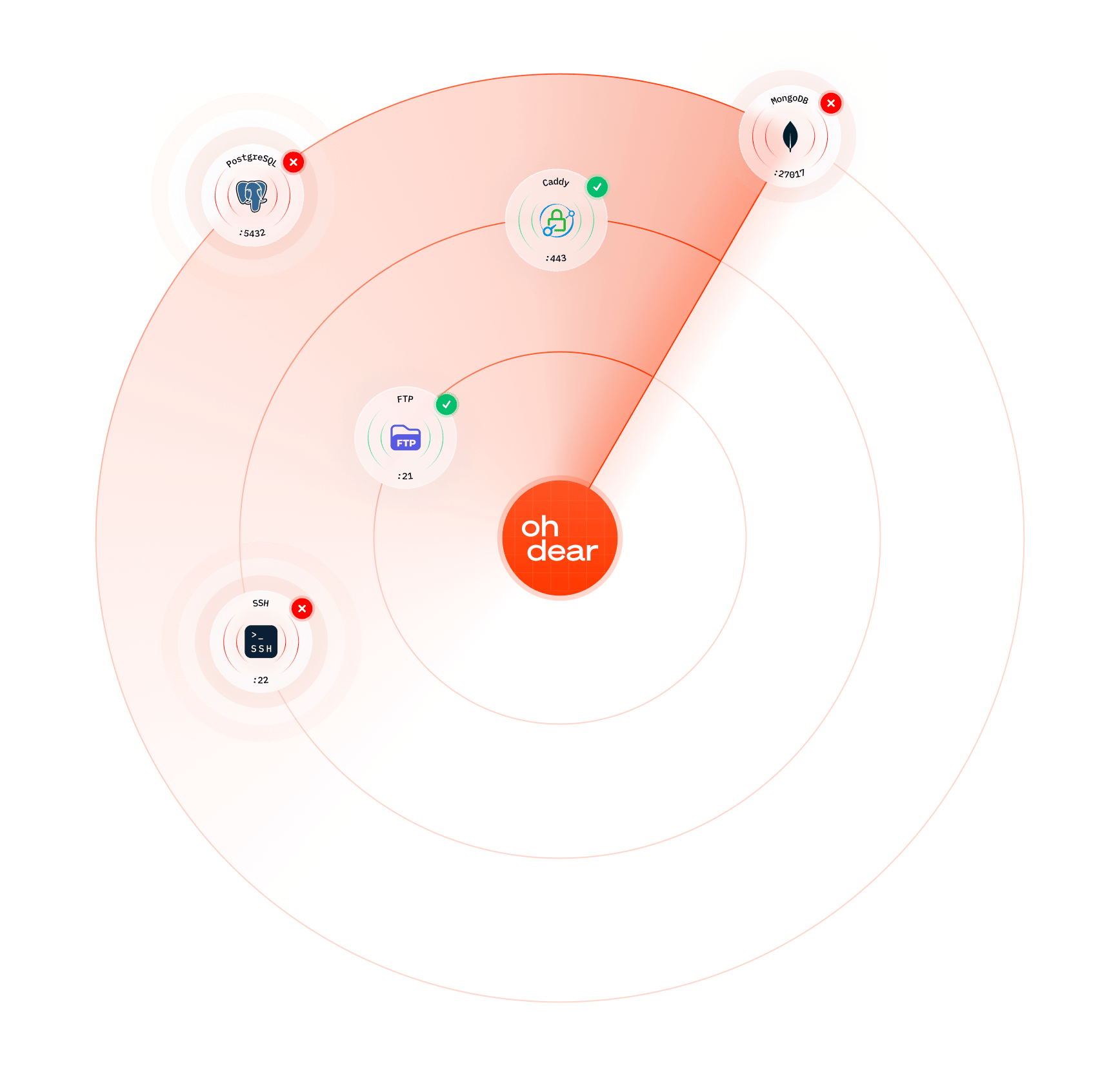
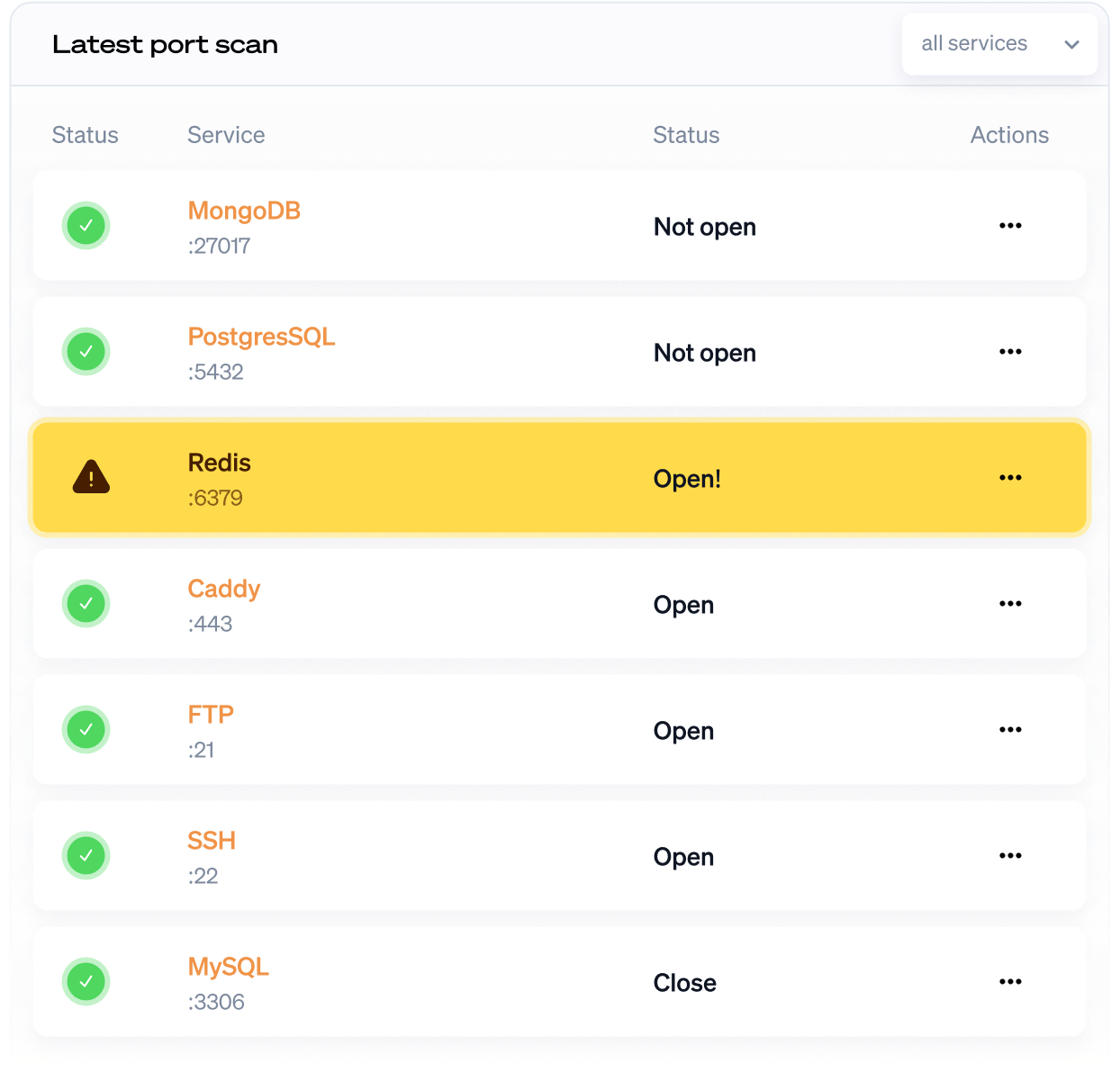
Team A exposes Redis or MongoDB without authentication - Team B assumed it was internal only. By the time anyone notices, attackers have already extracted your data. These services have no authentication by default, and a single misconfigured firewall rule exposes everything.
Forgotten SSH access on temporary servers left running for months. That "quick test server" from six months ago is still accessible, with weak credentials, running outdated software. It's an open door into your infrastructure.
Database ports open after firewall misconfiguration or cloud migration. A single change to your security groups accidentally exposes MySQL, PostgreSQL, or Redis to the entire internet. Without monitoring, you won't know until it's too late.
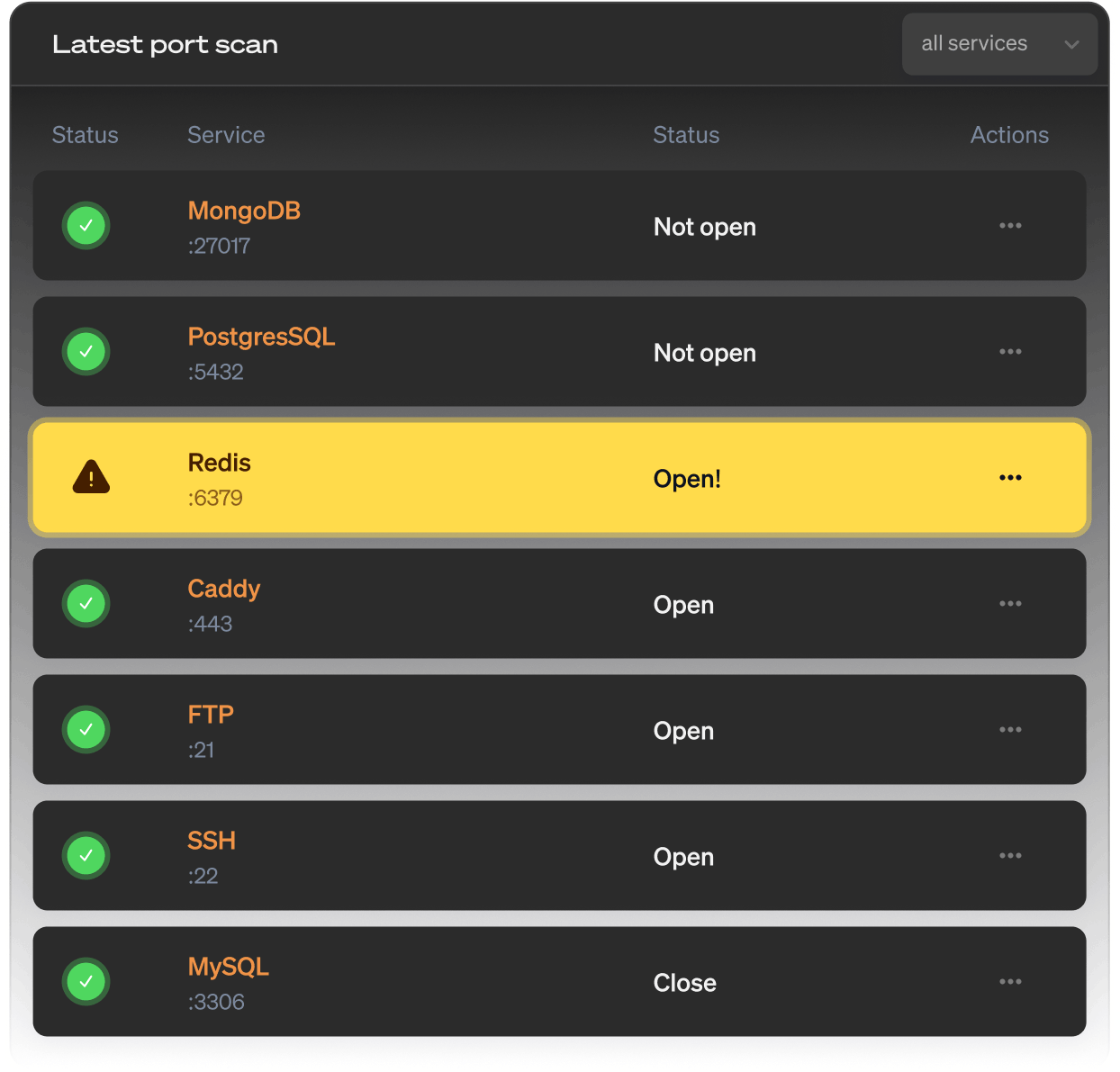
We check your servers hourly for unexpected open ports. Define which ports should be open and which must stay closed - we'll notify you the moment something changes.
Stop finding out from attackers
Manual port scans require remembering to run them. Most teams only think about port security during quarterly reviews, penetration tests, or after an incident. By then, exposed services may have been accessible for weeks or months.
Annual penetration tests miss changes in between. Infrastructure changes constantly - new servers, updated firewall rules, cloud migrations. A yearly pentest catches vulnerabilities at a single point in time, not the 364 other days.
We check every hour from multiple locations. Issues caught in hours, not months. No infrastructure to maintain, no commands to remember, no schedules to manage. Just continuous visibility into your attack surface.
When an unexpected port opens or an expected service goes down, you'll know immediately - not when a security researcher or attacker tells you.

Define your security baseline
Specify which ports SHOULD be open. For a web server, that's typically port 80 (HTTP) and 443 (HTTPS). For an email server, add 25, 587, and 993. We automatically detect your web ports and start monitoring them.
Specify which ports MUST be closed. Database ports (MySQL 3306, PostgreSQL 5432, MongoDB 27017), cache servers (Redis 6379, Memcached 11211), and remote access (SSH 22, RDP 3389) should typically not be accessible from the public internet.
Smart defaults for common scenarios. We know which ports are security-sensitive and suggest them for monitoring. Start with our recommendations, then customize based on your specific infrastructure needs.
Per-server configuration. A web server has different requirements than a database server or a jump box. Configure each server's expected state independently.
| Component | Value |
|---|---|
| Url | https://urlxyz.com |
| Error description | Operation timed out after 5001 milliseconds with 0 bytes received |
Downtime verified from Paris, France and Bangalore, India
Downtime verified from Paris, France and Bangalore, India
urlxyz.com has recovered after 2m. full report: https://ohdear.app/monitors/83/checks/411
urlxyz.com seems down! Error: HTTP/500 Downtown verified from Paris, France and Frankfurt
Pushover has been successfully enabled. We'll notify you when something goes wrong.
urlxyz.com has recovered after 2m. full report: https://ohdear.app/monitors/83/checks/411
urlxyz.com seems down! Error: HTTP/500 Downtime verified from Paris, France and Frankfurt
ntfy has been successfully enabled. We'll notify you when something goes wrong.
urlxyz.com has recovered after 2m. full report: https:/ohdear.app/monitors/83/checks/411
urlxyz.com has recovered after 2m. full report: https:/ohdear.app/monitors/83/checks/411
Text messages for urlxyz.com have been successfully enabled. We'll notify you when something goes wrong.
$_TOKEN="your API token" $ curl -X GET "https://notifyservicexyz.com/api/alert/urlxyzcom" \ -H "Authorization: Bearer $_TOKEN" \ -H "Accept: application/json" \ -H "Content-Type: application/json"
urlxyz.com has recovered after 2m. full report: https://app.opsgenie.com/monitors/83/checks/411
urlxyz.com seems down! Error: HTTP/500 Downtown verified from Paris, France and Frankfurt
Opsgenie has been successfully enabled. We'll notify you when something goes wrong.
urlxyz.com has recovered after 2m. full report: https://pagerduty.com/monitors/83/checks/411
urlxyz.com seems down! Error: HTTP/500 Downtown verified from Paris, France and Frankfurt
PagerDuty has been successfully enabled within Oh Dear. Notifications are enabled.
Choose how we let you know
Receive our notifications on your preferred platform. Via email, SMS, Slack, Discord, Opsgenie, Microsoft Teams, Pushover, ntfy, webhooks,… we can notify you wherever your team is active.
Take notifications to the next level: only notify who needs notifying by assigning responsibilities to different team members.

Compliance made continuous
PCI-DSS Requirement 11.3.2 requires regular external vulnerability scans. Port scanning is a fundamental part of vulnerability assessment. Continuous monitoring exceeds the quarterly minimum requirement.
SOC 2 requires continuous security monitoring and evidence of vulnerability management. Automated port scanning with alerting provides audit trail evidence that your organization actively monitors for security gaps.
ISO 27001 requires organizations to implement vulnerability management processes. Port monitoring demonstrates proactive identification of potential security weaknesses.
Audit-ready evidence. Our monitoring logs and alerts provide documentation for compliance audits, showing consistent security monitoring across your infrastructure.
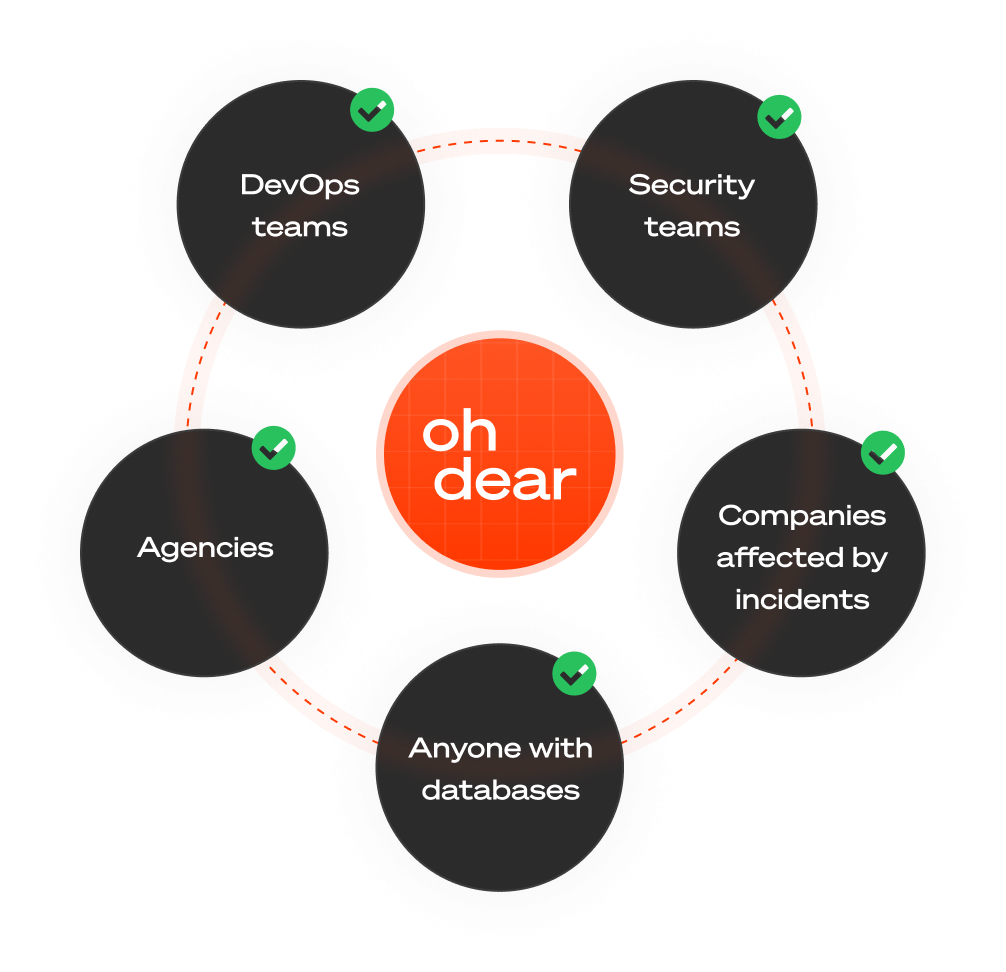
Who needs port scanning?
DevOps teams managing cloud infrastructure where security groups, firewall rules, and network configurations change frequently. One misconfiguration can expose entire clusters.
Security teams maintaining compliance who need continuous evidence of vulnerability monitoring for audits and certifications.
Agencies managing client servers who are responsible for client infrastructure security. Your reputation depends on keeping client systems secure.
Companies after security incidents who need to ensure vulnerabilities don't reappear. After a breach, continuous monitoring catches regression.
Anyone with databases, cache servers, or remote access that should never be accessible from the public internet. One exposed Redis instance can compromise everything.
Stop worrying, start monitoring
Start a no-strings-attached 10-day free trial. You're all set in less than a minute. (No credit card needed.)
Not convinced yet? Need help? Get in touch via [email protected].
How it works
Lightweight, continuous, from known IP addresses
Lightweight TCP connection checks
We attempt to establish TCP connections to your specified ports. No full vulnerability scan or service fingerprinting - just clean, fast detection of whether a port accepts connections.
Hourly checks from known IP addresses
Our scanning IPs are published at /used-ips. You can identify our requests in logs and firewall rules. No need to whitelist us - we check what the public internet can see.
Two-failure threshold prevents false alarms
Network glitches happen. We only alert after two consecutive failures, reducing noise while still catching real issues quickly.
IPv4 and IPv6, domains and IP addresses
Monitor your infrastructure however you address it. We support both IP versions and can resolve domains to check all associated addresses.
Wait, there's even more

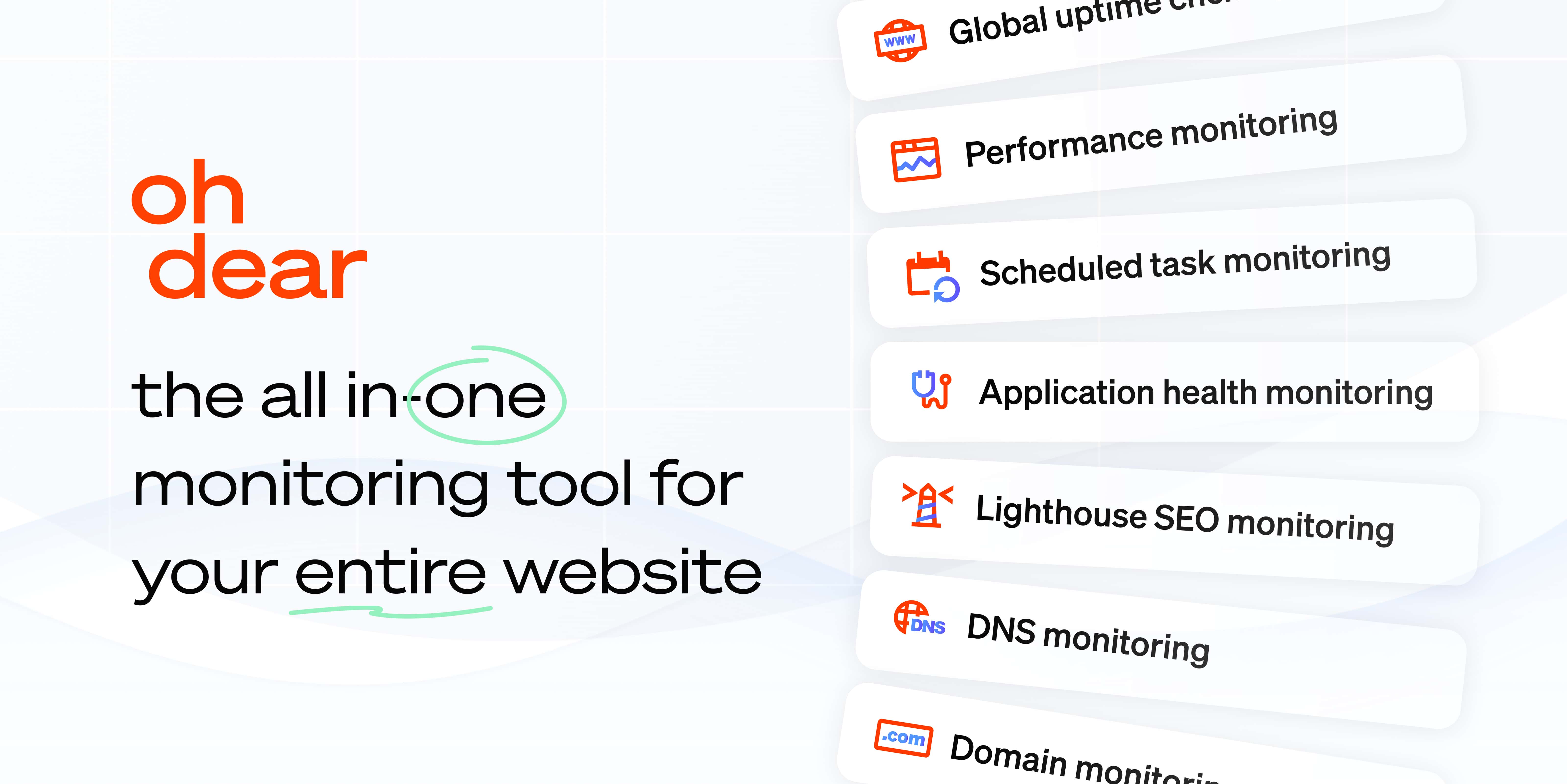
Continuous certificate monitoring
SSL certificates are essential in website security. We check all your certificate expiration dates & alert any change we detect.
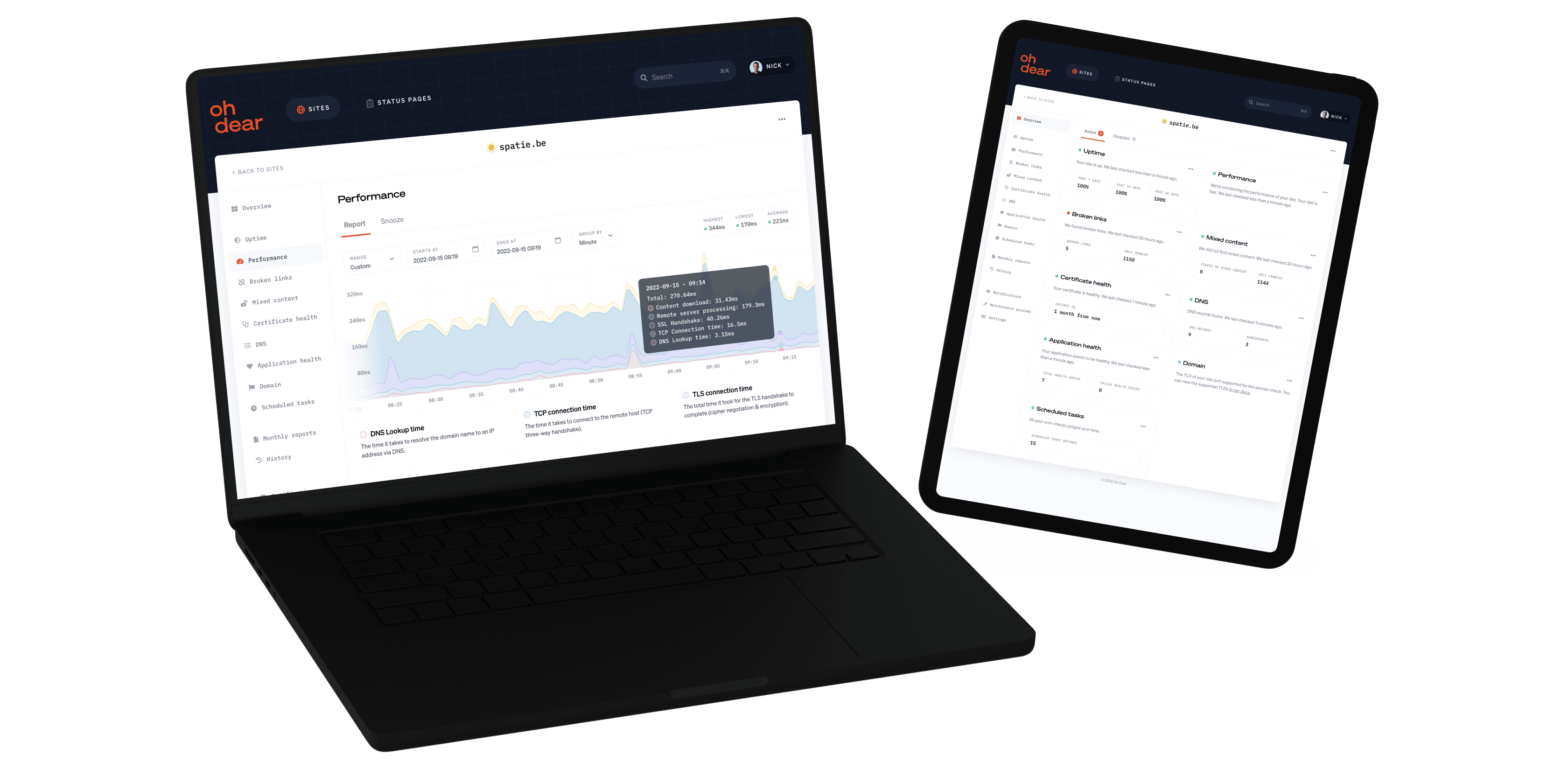
Performance monitoring
We provide highly detailed performance monitoring and insights. We'll notify you as soon as we detect your website is getting slow.
Fast and insightful notifications
Get notified instantly as soon as we detect an issue or an important change. Enable any channel you use, you're in full control.
Scheduled task monitoring
Your cron jobs (Linux) and scheduled tasks (Windows) are the heart of your data processing. We can monitor every single one of them.

Broken page & mixed content
We crawl and index your entire website, just like Google. As soon as we detect a broken link on your site we will let you know.
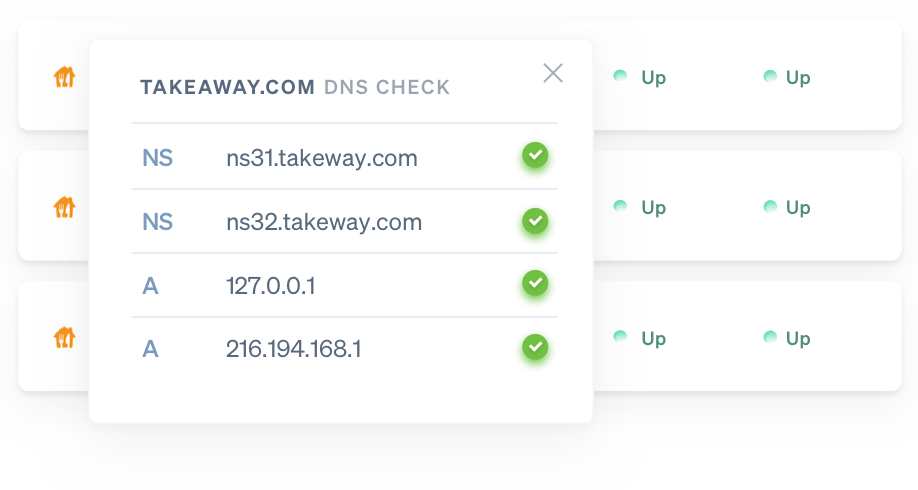
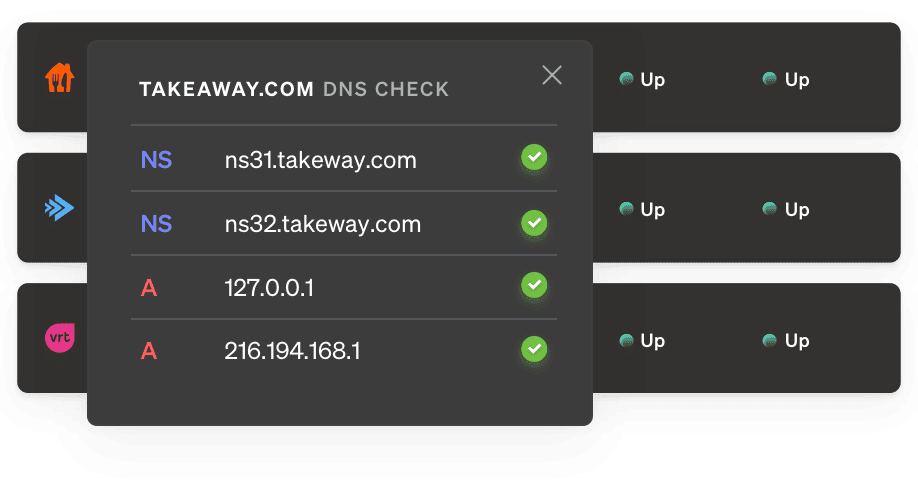
DNS record monitoring
Receive a notification whenever your DNS records are modified - intentionally or maliciously - so you can act and verify faster.


Application health monitoring
A lot can go wrong inside your app and server. Disk space may fill up, or the database may go down. We'll notify you when something is off.
Beautiful public status pages
In times of crisis, a public status page allows you to communicate to your clients. We'll host your status page so it's always available.
Website uptime monitoring
When your website goes down we'll let you know instantly. Now you can act before your or your client's brand reputation takes a hit.
Domain monitoring
We can check how long your domain is still registered. If your renewal date is close, we'll notify you. This will avoid you losing your domain.
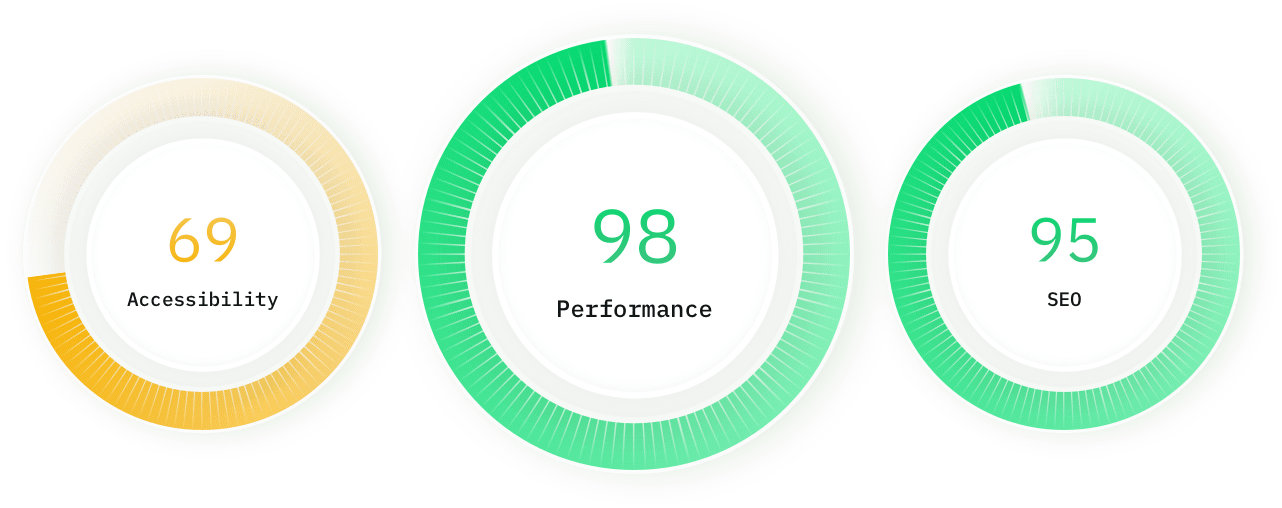

Lighthouse SEO monitoring
We track the speed & performance of your website over time. If we detect your website is suddenly slower, we'll let you know.
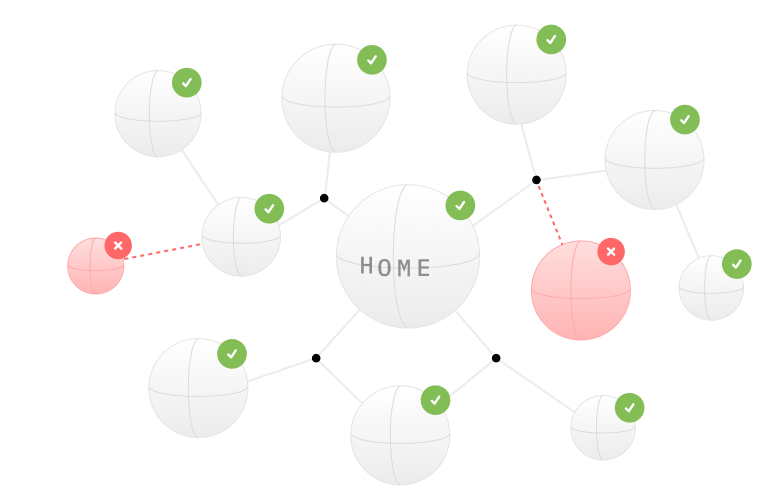
Sitemap monitoring
Elevate your SEO strategy and optimize your site. We analyse your sitemap health and check every URL for broken links.
Describe what you want to monitor
AI monitoring
Use AI to verify anything you want on your websites and services with Oh Dear's AI monitoring feature.
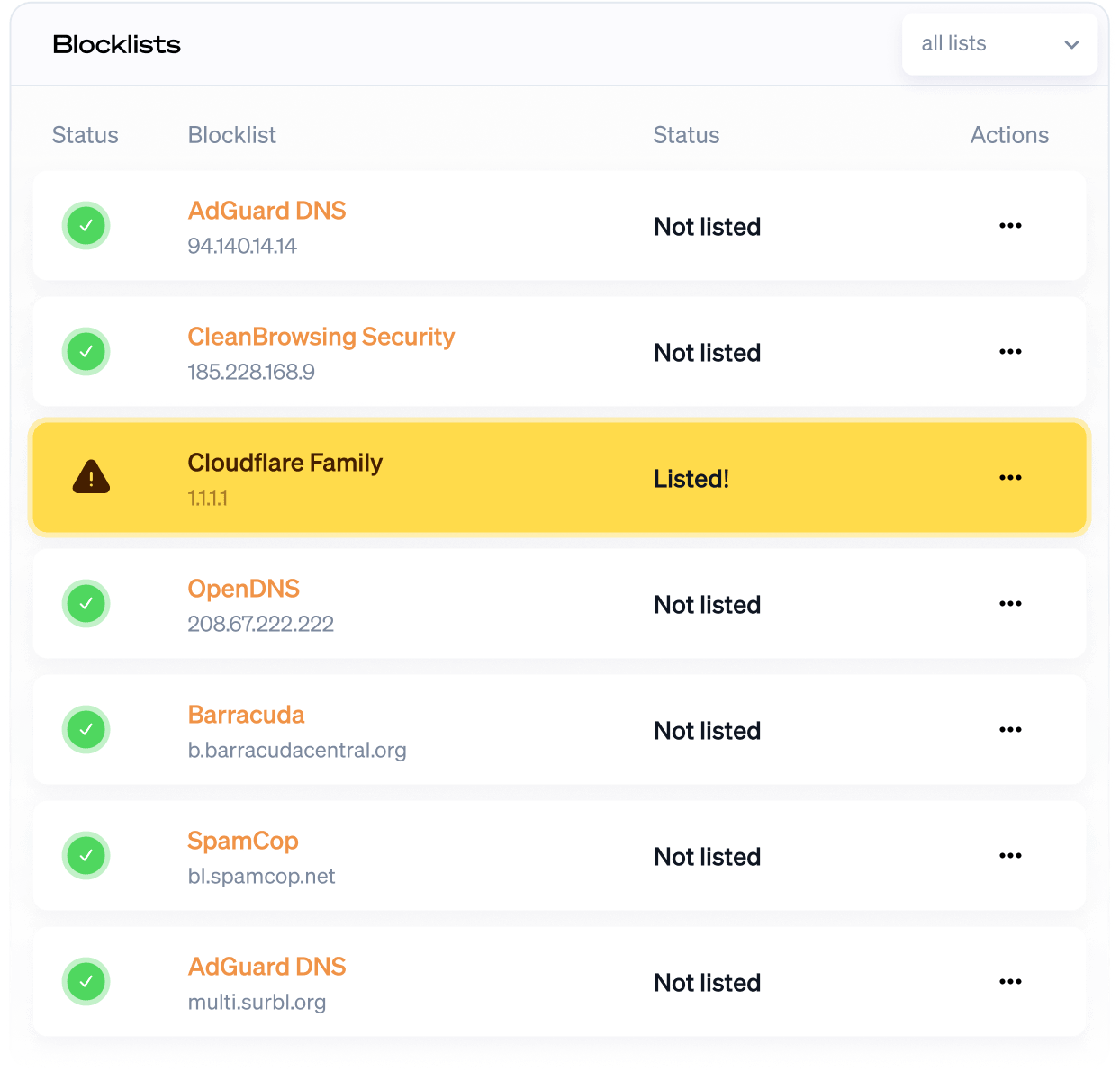
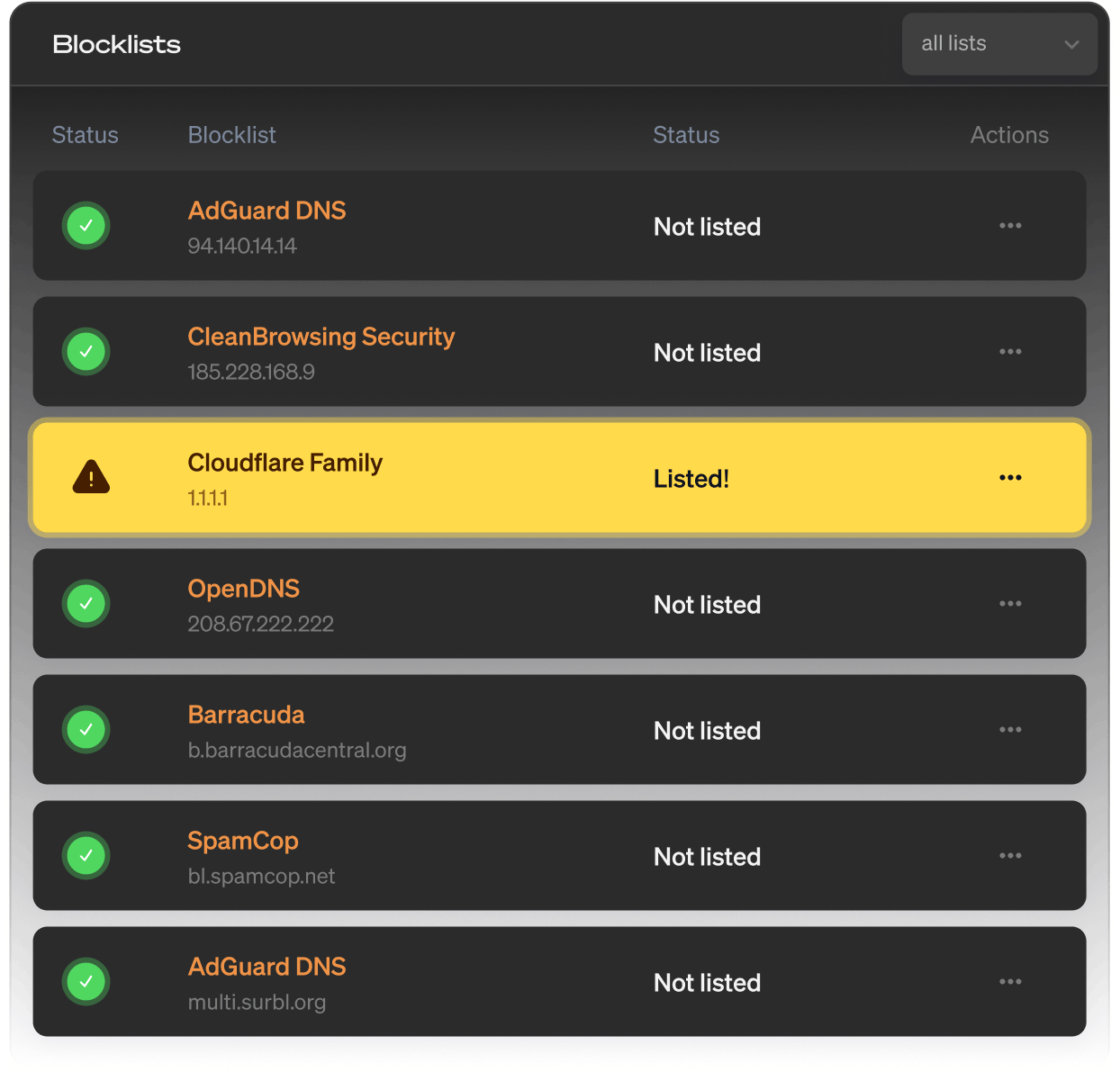
DNS blocklist monitoring
DNS blocklist monitoring helps you stay off spam and ad-block lists. Get notified when your DNS is blocked by a blacklist.
Start monitoring instantly
Start a no-strings-attached 10-day free trial. You're all set in less than a minute. (No credit card needed.)
Not convinced yet? Need help? Get in touch via [email protected].